15
+
YEARS OF
EXPERIENCE
1000
+
SUCCESSFUL
Projects
80
+
Satisfied
Clients
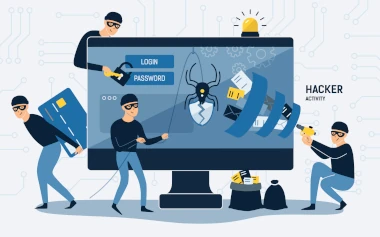
When relocating a business, it’s crucial to consider the cybersecurity implications of such a move. Re-installing or setting up a new network infrastructure, equipment, malware prevention systems, and new policies and procedures can all spell serious risks for cybersecurity and business continuity.
To ensure a smooth transition with minimal cybersecurity risks, turn to Proxar IT Consulting. We’ve helped many UK businesses defend their computers, servers, networks, systems, mobile devices and company data from malicious attacks. In order to do this, there are many key considerations
Secure Configuration
It’s not enough to have the right equipment in place. You need the policies and procedures to protect it. It’s vital to ensure your practices of configuration management, system management, endpoint management and compliance management are regularly reviewed and up to scratch. Relocating to a new environment can be the perfect time to revisit these policies and ensure adherence to best practice, alongside performing patching to further reduce risk. Proxar are well-versed in the best configuration practices and will help you tailor the necessary measures to your business and stay up to date with the latest trends.
Network Security
It’s important to secure your network in line with best practices. Proxar can help you install and use a Firewall, which will deny any unnecessary connections (whether inbound, outbound, to services, objects or networks). As a result, you can maximise the security of your network. When this is combined with an efficient network monitoring system, cybercriminals will find it much harder to breach your network undetected.
Malware Prevention
Malware prevention adds additional security to devices and services, helping to detect and protect your business by blocking or quarantining suspicious activity or trends. This doesn’t have to be a sole AntiVirus: various vendors can help protect Emails, networks, IDS, Firewalls and more. To help you navigate the many different providers and purposes, Proxar IT Consulting will work with your business to identify the right fit for you.
Incident Management
Incident management is all about having a process in place so that if an unfortunate incident does occur, your business can restore service and functionality as quickly as possible with minimal impact. This is multifaceted, and can depend on your office environment and new structures.
User Education and Awareness
Users are the first line of your cybersecurity defences. Training users about Cybersecurity awareness and the policies your business have implemented to protect in case of an attack or breach is vital. Luckily, Proxar IT Consulting helps UK companies work towards becoming Cyber Essentials Compliance accredited, ensuring they have the best standards across their business.
Remote and mobile working
The rise of remote working has led to new cybersecurity challenges. Home networks are often unsecured, as are those of coffee shops, leading to an increased risk of cyberattacks. At Proxar, we work with businesses to ensure that flexible working doesn’t compromise cybersecurity by helping to ensure remote and mobile workers access their data on a secured network. This results in greater control and reduces the risk of attacks on unsecure networks which fail to meet business standards.
Managing User Privileges
Granting users with the minimal access privileges in order to do their job is a fundamental part of cybersecurity. Giving only administrators the highest privileges reduces the risk of data breaches through hacking. However, without the support of a professional IT company, it can be complicated to understand who should have what access, particularly when relocating offices, which often results in new staff structures.
Monitoring
An approach giving complete visibility to all systems, services and outages ensures issues can be investigated as soon as detected rather than when reported by the business ensuring best cybersecurity practices are followed.
Removable media controls
Preventing users from being able to use, connect, run, install or copy data from a removable media device can protect your infrastructure should it contain malware. Relocations may come with new media devices: it’s important to ensure these are properly secured.
What next?
If you’re relocating offices in London or any other UK location, and would like additional guidance as to what this means for your cybersecurity, get in contact with Proxar IT Consulting today.








Choosing a reliable IT Relocation Service Provider
When it comes to choosing a reliable IT relocation service provider, there are several key factors to consider to ensure a smooth and successful transition. Firstly, look for a provider with a proven track record in handling IT relocations, as experience is crucial in avoiding potential pitfalls and ensuring a seamless move. Additionally, consider the range of services offered by the provider, such as packing, transportation, and setup, to determine if they align with your specific needs. It’s also important to check reviews and testimonials from previous clients to gauge the provider’s reputation and level of customer satisfaction. By taking these factors into account, you can make an informed decision and choose a trustworthy IT relocation service provider for your upcoming move.
schedule a call

answer time
satisfaction
score
on initial call
same business
day










