15
+
YEARS OF
EXPERIENCE
1000
+
SUCCESSFUL
Projects
80
+
Satisfied
Clients
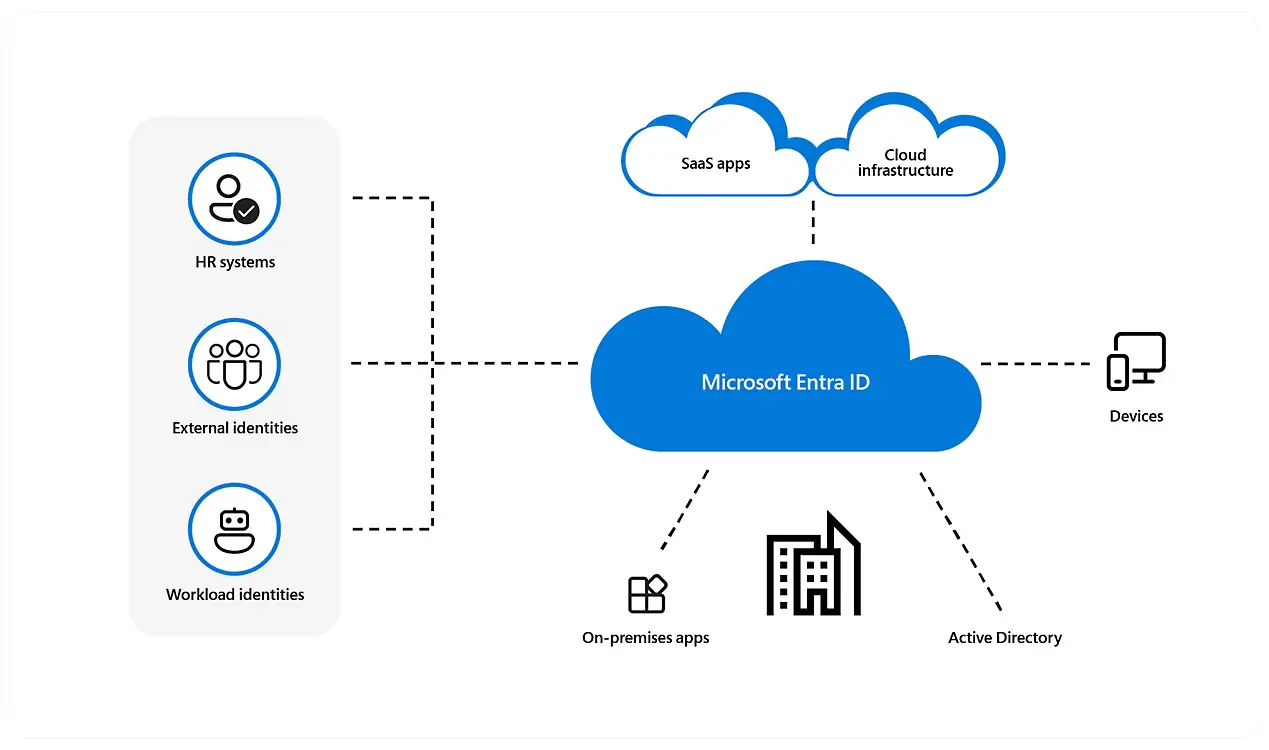
In today’s rapidly evolving digital landscape, safeguarding identity and access management is critical for enterprises navigating complex cybersecurity threats. Entra ID, Microsoft advanced identity platform, offers robust features that protect organizational assets while enabling seamless user experiences. Understanding and implementing Entra ID security best practices can significantly reduce vulnerabilities and fortify defenses against unauthorized access. This article explores thorough strategies, real-world insights, and actionable tips for optimizing Entra ID deployment to secure your business effectively.
Core Entra ID Security Best practices for Modern Enterprises
Identity and access management is the cornerstone of enterprise security, and Entra ID provides a comprehensive solution designed to address this need. Embracing core Entra ID security best practices begins with robust authentication measures, such as implementing multi-factor authentication (MFA) across all user accounts. MFA drastically reduces the risk of compromised credentials by requiring additional verification beyond passwords. Additionally, enforcing strong password policies, including complexity requirements and regular rotation schedules, further strengthens user account protection. Utilizing Conditional Access policies allows organizations to create granular controls tailored by user risk profiles, device compliance, location, and session risk. These policies ensure that only legitimate users and compliant devices gain the appropriate level of access dynamically.
Role-based access control (RBAC) should also be employed to limit permissions strictly based on job responsibilities, minimizing exposure from privilege escalation or unnecessary access rights. Monitoring and logging user activities through Entra ID’s advanced audit logs and integrating alerts with Security Information and Event Management (SIEM) systems provide proactive detection of suspicious activity. Collectively, these foundational practices help maintain a secure environment by reducing attack surfaces and enabling rapid incident response, establishing a resilient identity ecosystem tailored for organizations of all sizes.







Advanced Entra ID Security Best Practices to Enhance Organizational Shielding
Protecting digital identities requires more than basic configurations. Here’s a structured approach to implementing advanced Entra ID security practices, combining technical controls with human awareness for maximum protection.
- Implement Privileged Identity Management (PIM): Use PIM to enforce just-in-time access, granting administrative privileges only when necessary and for a limited time. This reduces standing access and minimizes the risk of internal misuse or external compromise.
- Conduct Regular Access Reviews: Pair PIM with scheduled reviews of user access to ensure ongoing compliance with the principle of least privilege. Automate these reviews to maintain oversight without manual effort.
- Use Risk-Based Conditional Access: Leverage AI-powered insights from Microsoft Defender for Identity to detect anomalies such as suspicious sign-ins or impossible travel. Automatically enforce stronger authentication or access restrictions in real time.
- Deploy Entitlement Management: Simplify identity governance by automating onboarding, offboarding, and access lifecycle management. This ensures users only retain permissions they currently need.
- Maintain Policy Balance: Ensure that access policies are effective without disrupting user productivity. Avoid overly aggressive rules that can cause friction while still maintaining high security standards.
- Enhance Logging and Monitoring: Configure comprehensive logging for all access and identity-related activities. Use analytics to gain visibility without overwhelming your team with data noise.
- Invest in User Training: Conduct regular security awareness training, including simulated phishing exercises. Human vigilance is a critical layer of defense that complements technical controls.
At Proxar IT Consulting, we help organizations implement these advanced Entra ID security measures tailored to their unique needs. Our expert-led approach ensures maximum protection without compromising usability, giving you full confidence in your digital identity infrastructure.

Advanced Entra ID security features such as Privileged identity Management and AI-driven Conditional Access policies provide organizations with a dynamic and responsive defense posture. Proactively managing administrative privileges and leveraging real-time risk signals create a more resilient and adaptable identity framework. Though, balancing stringent security with user experience is critical, which makes expert guidance essential for designing effective policies that protect assets while maintaining productivity.
Real-World Entra ID Security Best Practices: Case Studies and Implementation Success
Examining real-world implementations illuminates the tangible benefits and practical approaches to Entra ID security best practices. One multinational financial institution, for example, partnered with Proxar IT Consulting to overhaul their identity infrastructure. By deploying MFA and Conditional Access policies customized for high-risk transactions and remote access, they reduced compromised credentials incidents by over 70% within six months. The integration of Privileged Identity Management also minimized privileged account exposure, delivering compliance with stringent industry regulations.
In another case, a rapidly growing technology firm implemented Entitlement Management to automate employee onboarding and offboarding. This automation eliminated manual errors in access provisioning, reducing internal risk and accelerating new hire productivity. The continuous access reviews helped the security team identify and revoke dormant user rights promptly.
These case studies underscore the importance of a tailored approach to Entra ID security, balancing automation, policy enforcement, and ongoing monitoring. Proxar IT’s consultants work closely with clients to design scalable frameworks that align with operational objectives and compliance mandates. Our methodical approach includes assessment, policy configuration, user training, and continuous optimization, ensuring sustainable security improvements.
By learning from accomplished deployments and collaborating with trusted partners like Proxar IT Consulting, organizations gain confidence in their Entra ID strategy, achieving a secure and agile identity environment that supports their digital conversion goals.

answer time
satisfaction
score
on initial call
same business
day
Empower Your Organization with Effective Entra ID Security Strategies
Incorporating Entra ID security best practices into your identity management framework is essential to protecting digital assets in today’s complex threat landscape. From foundational measures like MFA and Conditional Access to advanced capabilities such as Privileged Identity Management and Entitlement management, each layer serves to strengthen your organization’s security posture while enabling seamless user experiences. Partnering with experienced IT consulting professionals like Proxar IT Consulting ensures that your entra ID deployment is optimized, sustainable, and tailored to your unique business needs.
Don’t leave your organization’s security to chance-connect with us to explore how we can help you implement robust entra ID security strategies that align with industry standards and compliance requirements. Visit our contact us page to get expert assistance and take the first step towards a more secure digital identity ecosystem.

